Contacts | Feedback | Help | Privacy | About US Copy Rights Reserved Bellacom Technologies LLC 2006-2012
What is Risk Assessment and Compliance?
-
Security risk assessment identifies and documents vulnerabilities in your environment and develops a remediation plan to eliminate those vulnerabilities.
Security compliance establishes protocols to protect data confidentiality, prevent unauthorized access to information and comply with policies required by audits, regulatory acts and international standards.
Security breaches related to the numerous regulations a company must adhere to have received a lot of press. While these regulations represent good security practices, they can seem overwhelming and unmanageable. The good news is that maintaining security compliance is not as complex as it may seem. Regulatory guidelines often provide a blueprint that can easily be incorporated into your existing security management policies.-
Misguided Peace of Mind. Solved.
See how our Data Loss Assessment can help protect your business from threats both inside and out
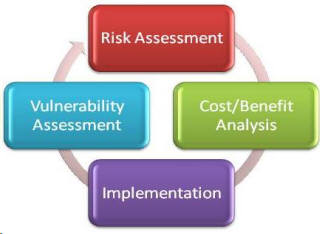
Risk Assessment
A comprehensive risk assessment carefully identifies and documents the vulnerabilities in your security environment, and then recommends a remediation plan to close the gap. It's generally a best practice to work with a third party to ensure the most objective view into your environment.
-